HTTPS Proxy for the G4 iMac
In my previous post, the footnotes mentioned one of the biggest challenges when using old systems online today: their outdated versions of security protocols like SSL are usually unsupported by modern services.
For example, may websites today (including my own blog), require the use of HTTPS connections. This is a fairly standard practice across the internet today, but for older browsers like Safari on OS X Tiger, this is a problem. The SSL protocols supported in that browser are no longer used by most modern webservers due to vulnerabilities that are mitigated in newer versions.
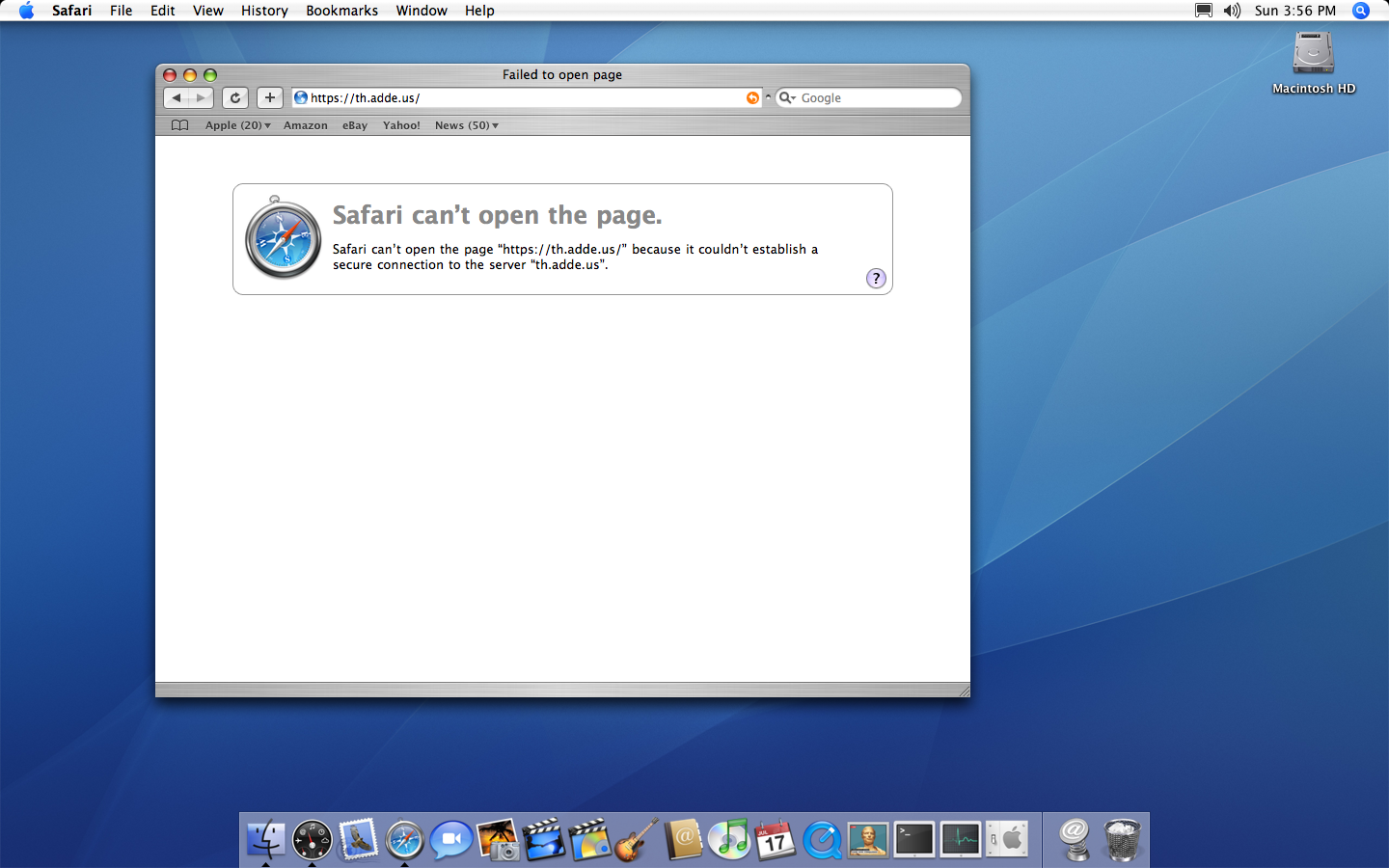 Safari is unable to establish a secure connection to my website, which requires HTTPS connections.
Safari is unable to establish a secure connection to my website, which requires HTTPS connections.
When you try and load a modern website over HTTPS in an old version of Safari, you’re greeted with an error message like this:
Safari can’t open the page “https://th.adde.us” beacuse it couldn’t establish a secure connection to the server “th.adde.us”.
An Idea
While I was setting up a network connection on the G4 yesterday, I took a detour through a couple of the lesser-visited tabs like AppleTalk, reminscing about days of old. Then the Proxies tab triggered an idea.
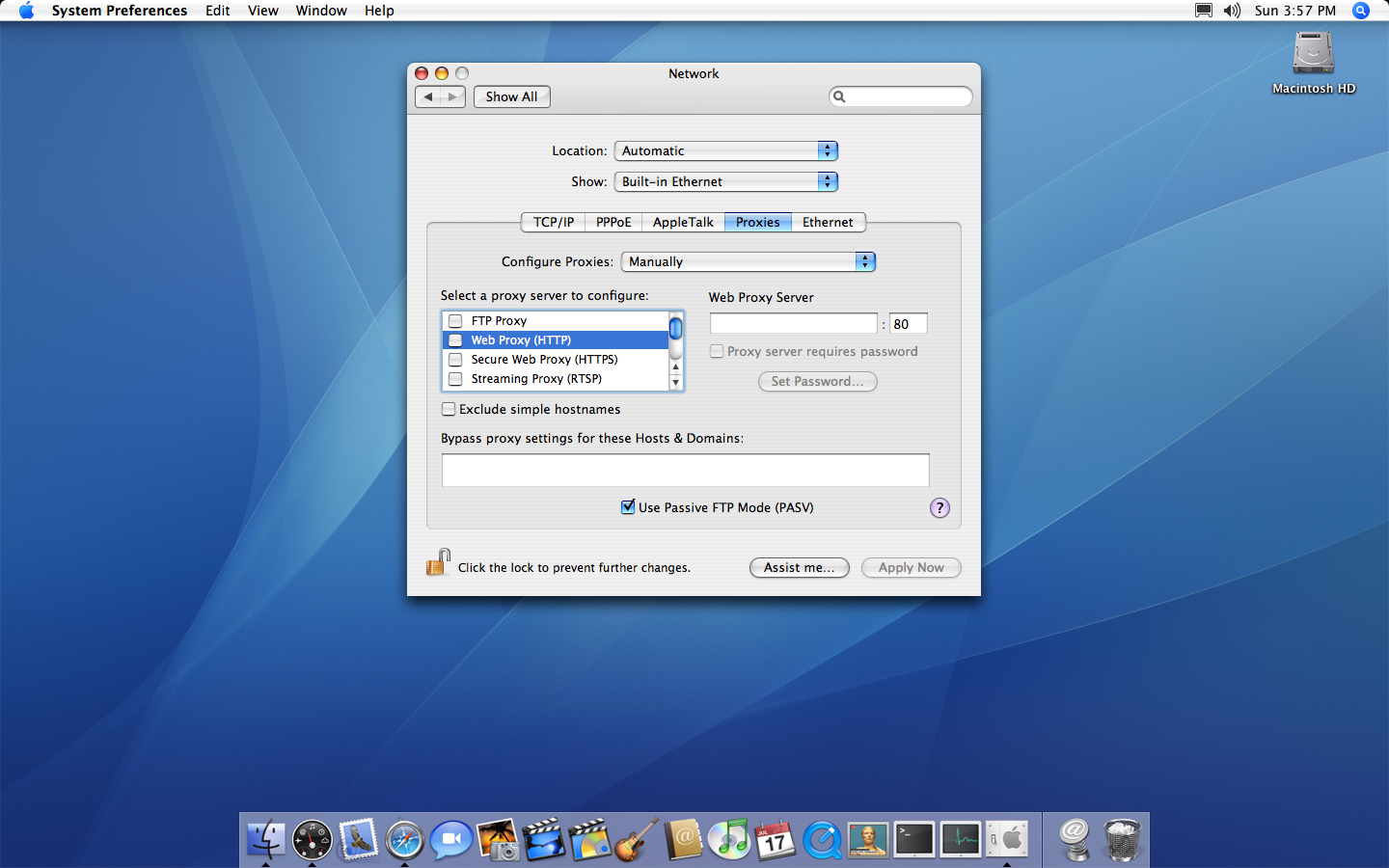 Mac OS X Network Preferences Panel
Mac OS X Network Preferences Panel
What if I set up a proxy on my local network that handled HTTPS, and then provided an insecure interface for the iMac to connect to?
… in effect making it possible for the old version of Safari to communicate with modern web servers?
After a few minutes of Googling, I found a fork of macproxy, a Python script that implements a simple proxy that does exactly what I had in mind.
Macproxy Docker Image
To be totally honest, Python is kind of a mess these days (IMHO). I always seem to have the wrong version on my system, a messed up virtualenv, or some other kind of compatibility drama. Like Ruby, Python feels really complicated if you don’t use it every day, so I try and avoid it for the most part.
Since I use python so infrequently and Macproxy has pretty clean requirements (python3 and a small handful of modules), it seemed like a good candidate for a container. I’ve been using Docker a lot recently at work to deal with these kinds of scenarios and it’s been wonderful.[1]
I ran the proxy on my Macbook Air for a few minutes with Docker and tested it with the iMac. It worked great, and I was pretty excited. But I didn’t really want to run the proxy on my laptop all the time.
I really wanted to be able to (easily) run it from my Synology NAS.
So I published an image on Docker Hub.
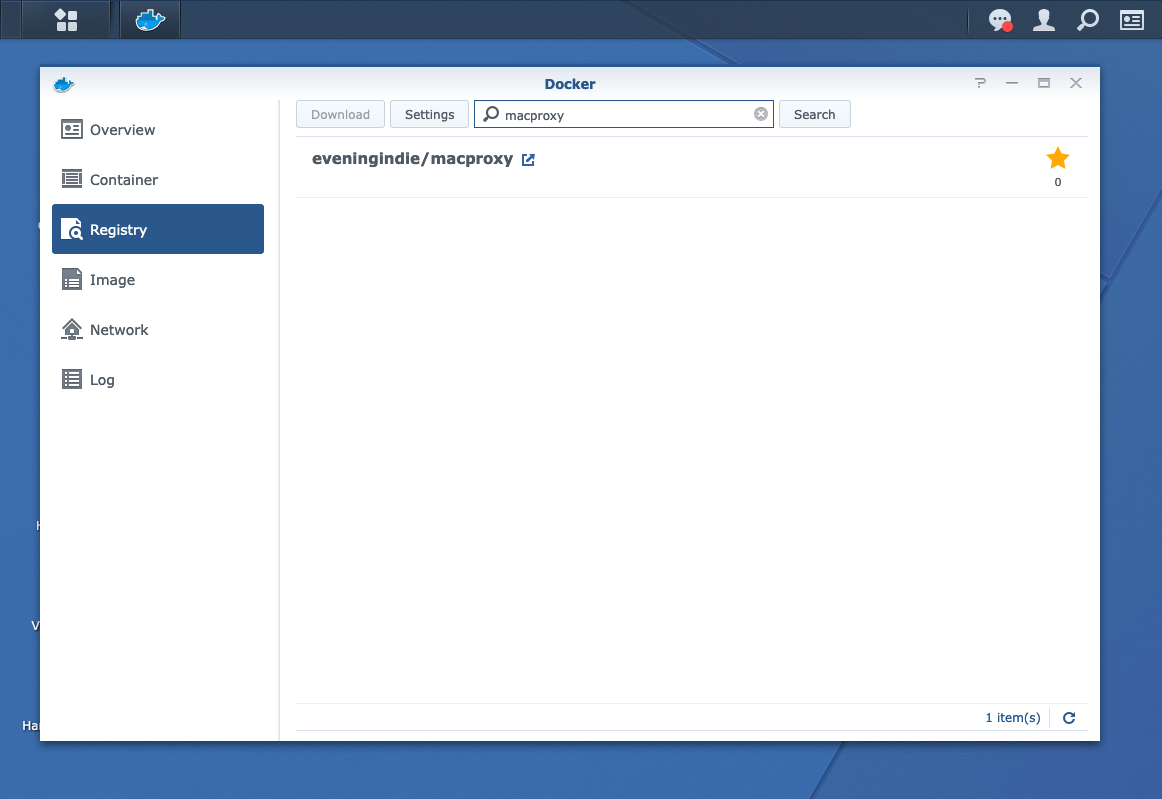 Searching the Registry in Synology's Docker app returns my image.
Searching the Registry in Synology's Docker app returns my image.
With the image published, I was able to simply search the Docker registry for my image, which I could then Download right in the Synology Docker app.
Once downloaded, creating a local container with the image is a breeze.
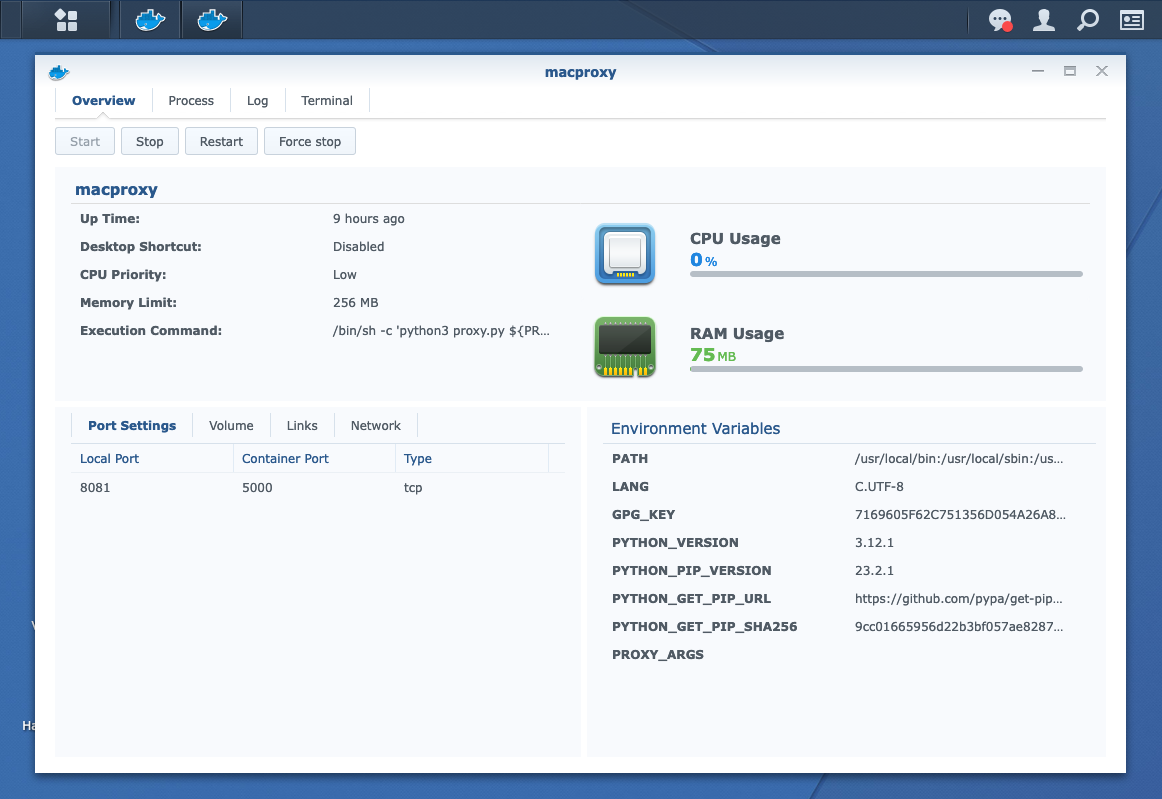 macproxy container running on Synology
macproxy container running on Synology
By default, the proxy listens for connections on port 5000. My Docker image supports passing command line args to the script through the PROXY_ARGS environment variable, but I’m opting to map port 5000 to 8081 on my NAS.[2]
iMac Configuration
With the image published and a container running on my local network, I turned to finalizing configuration on the iMac.
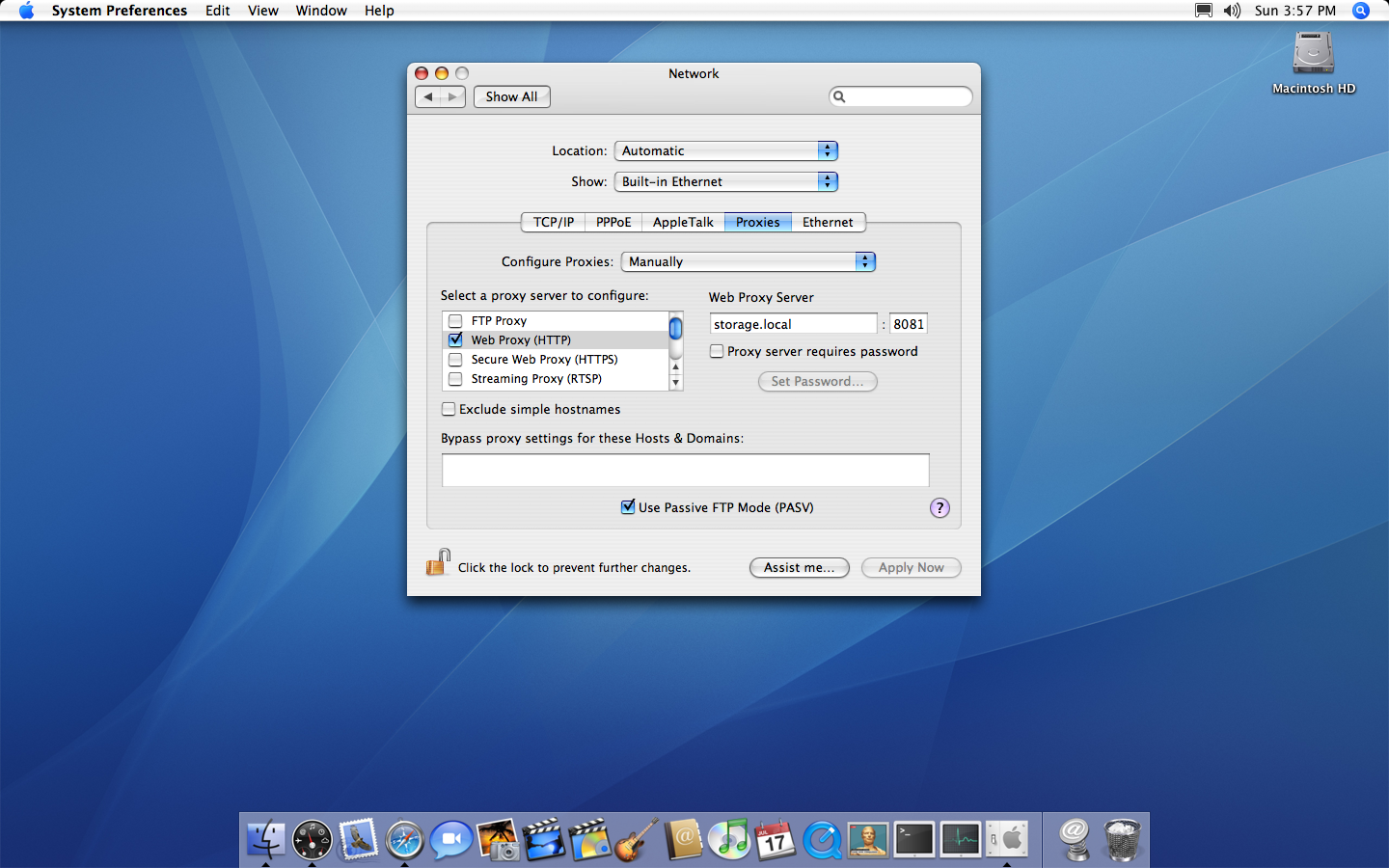 Updated Network Proxy settings
Updated Network Proxy settings
For the Web Proxy (HTTP) Server, I specified the hostname of my NAS (storage.local)[3], as well as the port number I’d mapped to the container (8081). With this configuration applied, the iMac will now send web requests from Safari through the NAS using an insecure connection[4]. The proxy will relay requests to the upstream host via HTTPS, then modify the responses it receives and send them back to the iMac.
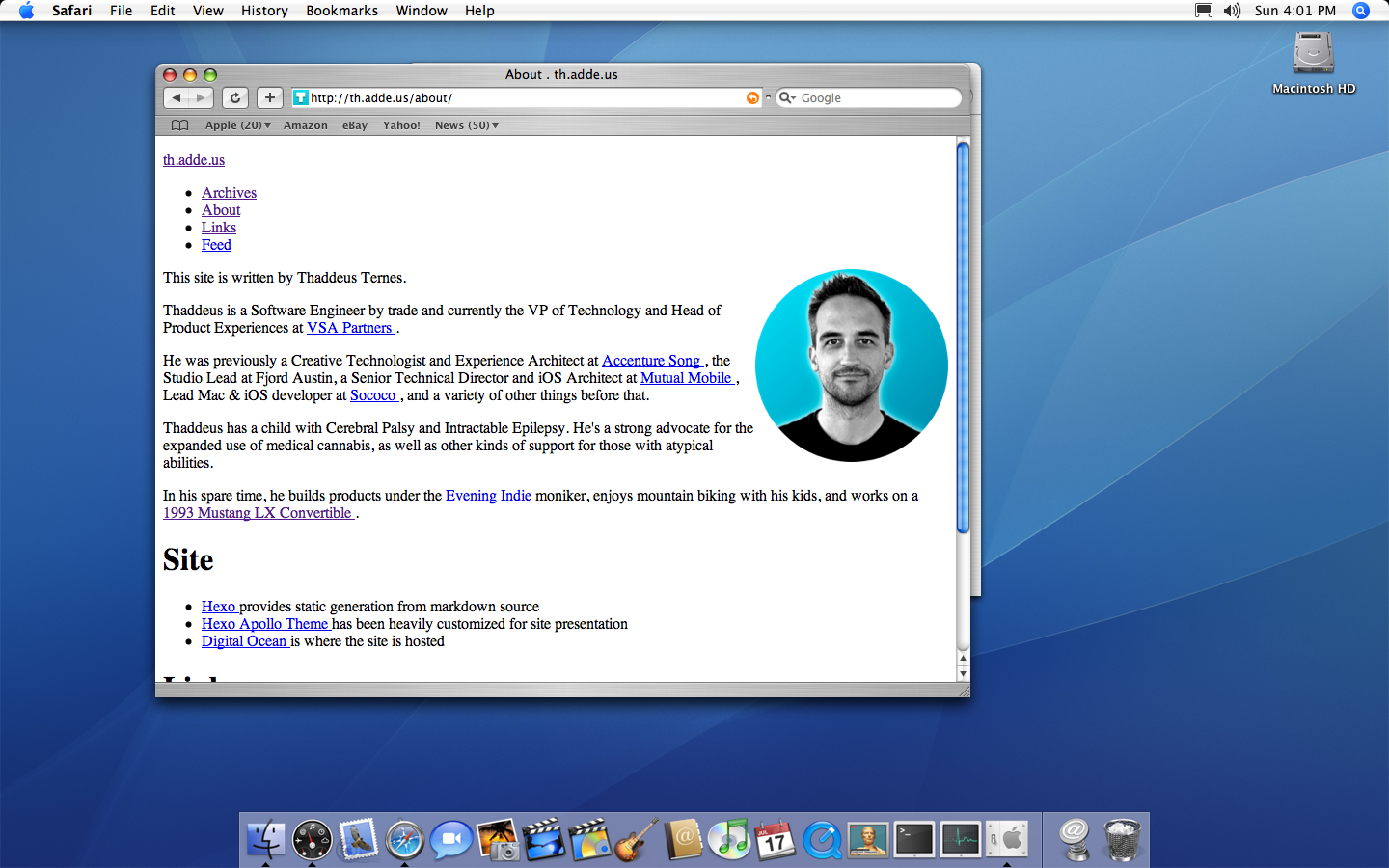 Safari displaying my website without HTTPS
Safari displaying my website without HTTPS
Success! 🎉
Macproxy also strips a handful of HTML tags and modifies the source a bit with help from the BeautifulSoup module, so most pages look fairly vanilla, but they’re usually somewhat usable (especially when a solid document hierarchy is in place with basic HTML).
With this in place, I was able to download a copy of LineIn from Rogue Amoeba’s Legacy page without having to use modern devices.
Now it’s time to find a copy of my blog from 2004.
Long live Web 1.0.
I should write up some of the quick tips I’ve been using for creating clean environments with Docker, especially for legacy NodeJS applications 🤔 ↩︎
8081 just feels like a good port number for a proxy ↩︎
It’s pretty great that OS X supports multicast DNS names at this level of system configuration. mDNS and Bonjour still shine in terms of how simple and effective they are in creating great experiences. ↩︎
Obviously this should not be used for anything confidential or sensitive! I’m pretty comfortable with my casual browsing requests being transmitted over my personal local network, but definitely don’t run this on a public-facing host ⚠️ ↩︎